§ ToIP General Glossary
Specification Status: Public Review Draft 01 (PR1)
Latest Draft:
Editors:
Contributors:
Participate:
§ Status
This is the first public review draft of the ToIP General Glossary. It is also the first version published using the Spec-Up-T specification editing utility based on Spec-Up specification editing utility developed by the Decentralized Identity Foundation.
§ Copyright Notice
This specification is subject to the OWF Contributor License Agreement 1.0 - Copyright available at https://www.openwebfoundation.org/the-agreements/the-owf-1-0-agreements-granted-claims/owf-contributor-license-agreement-1-0-copyright.
These terms are inherited from the Technical Stack Working Group at the Trust over IP (ToIP) Foundation. Working Group Charter
§ Terms of Use
These materials are made available under and are subject to the OWF CLA 1.0 - Copyright & Patent license. Any source code is made available under the Apache 2.0 license.
THESE MATERIALS ARE PROVIDED “AS IS.” The Trust Over IP Foundation, established as the Joint Development Foundation Projects, LLC, Trust Over IP Foundation Series (“ToIP”), and its members and contributors (each of ToIP, its members and contributors, a “ToIP Party”) expressly disclaim any warranties (express, implied, or otherwise), including implied warranties of merchantability, non-infringement, fitness for a particular purpose, or title, related to the materials. The entire risk as to implementing or otherwise using the materials is assumed by the implementer and user.
IN NO EVENT WILL ANY ToIP PARTY BE LIABLE TO ANY OTHER PARTY FOR LOST PROFITS OR ANY FORM OF INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES OF ANY CHARACTER FROM ANY CAUSES OF ACTION OF ANY KIND WITH RESPECT TO THESE MATERIALS, ANY DELIVERABLE OR THE ToIP GOVERNING AGREEMENT, WHETHER BASED ON BREACH OF CONTRACT, TORT (INCLUDING NEGLIGENCE), OR OTHERWISE, AND WHETHER OR NOT THE OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
§ Introduction
The ToIP General Glossary is a deliverable of the ToIP Concepts and Terminology Working Group. Its purpose is to promote shared understanding of terms and concepts across the many different working groups, communities, enterprises, and ecosystems who are collaborating to develop and deploy decentralized digital trust infrastructure.
Contributions and feedback are encouraged from any stakeholder in this area of terminology.
§ Linking to this Glossary
This glossary is designed to be both human and machine readable. All terms are listed alphabetically; acronyms are listed separately and linked to the fully expanded terms. Document authors can link directly to any term using standard web links and anchors following this syntax:
https://trustoverip.github.io/ctwg-general-glossary#term:xxxxx
Where xxxxx is the term as it appears in the glossary, with any spaces are replaced by en-dashes (hyphens). For example, a link to the term self-certifying identifer would be:
https://trustoverip.github.io/ctwg-general-glossary#self-certifiying-identifier
A specification document written using the Trustoverip’s open source Spec-Up-T environment documented in the Spec-Up-T manual, originally based on Decentralized Identity Foundation’s open source Spec-Up editor.
The tool may create special external references to terms in this glossary using the Spec-Up xref and the tref tags following this syntax:
[ [xref: glossary, xxxxx] ] and [ [tref: glossary, xxxxx] ]
Note: we’ve put spaces between brackets to be able to present this literally; remove the spaces in use.
Where glossary is the text label the document author assigns to the URL of a Web-accessible glossary, and xxxxx is the term as it appears in that glossary, with any spaces are replaced by en-dashes (hyphens). For example, a Spec-Up external reference to the term self-certifying identifer using the label toip for this glossary would look like this:
[[xref: toip, self-certifying-identifier]]
An item borrowed from an other glossary might look like this:
[[xref: keri, duplicity]]
§ Referenced Glossaries
These glossaries have been interlinked using tref and xref tags. We show both test and production environments. The specs.json is for proficient users to inspect the production settings.
§ Interlinked glossary summary
| Glossary | TEST repo | Live TEST Glossary | Production repo | Live PRODUCTION Glossary | Specs.json PROD |
|---|---|---|---|---|---|
| KERIsuite | HenkvanCann | TEST | WebofTrust | PRODUCTION | Specs.json |
| vLEI | HenkvanCann | ||||
| ToIP Main | HenkvanCann | TEST | ToIP | PRODUCTION | Specs.json |
| ToIP General IT | HenkvanCann | TEST | ToIP | PRODUCTION | Specs.json |
The following glossaries were used as sources for some of the definitions in the ToIP General Glossary. All source glossaries are cited in the definitions of each term.
| Short Name | Source Glossary | URL |
|---|---|---|
| Wikipedia | Wikipedia | https://www.wikipedia.org/ |
| eSSIF-Lab | eSSIF-Lab Glossary | https://essif-lab.github.io/framework/docs/essifLab-glossary |
| NIST-CSRC | NIST Computer Security Resource Center Glossary | https://csrc.nist.gov/glossary/ |
| PEMC IGR | Kantara Privacy Enhancing Mobile Credentials Implementors Guidance Report | https://kantarainitiative.org/download/pemc-implementors-guidance-report/ |
| W3C DID | W3C Decentralized Identifiers (DIDs) 1.0 | https://www.w3.org/TR/did-core/#terminology |
| W3C VC | W3C VC Data Model 1.1 | https://www.w3.org/TR/vc-data-model/#terminology |
| Ethereum | Ethereum.org Glossary | https://ethereum.org/ |
| Merriam-Webster | Merriam-Webster Dictionary | https://www.merriam-webster.com/dictionary/ |
§ Terms and Definitions
- ADR (ADR)
- architectural-decision-record
- agency (agency)
- Agents can be people, edge computers and the functionality within wallets; the service an agent offers.
- API (API)
- application-programming-interface
- append-only event logs (append-only-event-logs)
-
Append-only is a property of computer data storage such that new data can be appended to the storage, but where existing data is immutable.
-
A blockchain is an example of an append-only log. The events can be transactions. Bitcoin is a well-known Append only log where the events are totally ordered and signed transfers of control over unspent transaction output.
-
More on Wikipedia
- application programming interface (application-programming-interface)
- An application programming interface (API) is a way for two or more computer programs to communicate with each other. It is a type of software interface, offering a service to other pieces of software.
- architectural-decision record (architectural-decision-record)
- Is a justified software design choice that addresses a functional or non-functional requirement that is architecturally significant.
- Source adr.github.io
- authentic web (authentic-web)
- The authentic web is the internet as a whole giant verifiable data structure. Also called Web5. The web will be one big graph. That’s the mental model of the ‘authentic web’.
- authenticity (authenticity)
-
The quality of having an objectively verifiable origin ; contrast veracity. When a newspaper publishes a story about an event, every faithful reproduction of that story may be authentic — but that does not mean the story was true (has veracity).
-
Authenticity is strongly related to digital security. Ideally it should be verifiable (to a root-of-trust). The future picture therein is the authentic-web.
- https://glossary.trustoverip.org/#term:authority
-
Is the function of specifying access rights/privileges to resources, which is related to general information security and computer security, and to access control in particular.
-
More formally, “to authorize” is to define an access policy.
- autonomic computing systems (autonomic-computing-systems)
- Self managing computing systems using algorithmic governance, from the 90’s way way way before DAOs. KERI creator Sam Smith worked at funded Navy research in the 90’s on autonomic survivable systems as in “self-healing” systems: “We called them autonomic way back then”.
- base64 (base64)
-
In computer programming, Base64 is a group of binary-to-text encoding schemes that represent binary data (more specifically, a sequence of 8-bit bytes) in sequences of 24 bits that can be represented by four 6-bit Base64 digits.
-
More on source Wikipedia
- BFT (BFT)
- byzantine-fault-tolerance
- blake3 (blake3)
- BLAKE3 is a relatively young (2020) cryptographic hash function based on Bao and BLAKE2.
- branch (branch)
- In software development a ‘branch’ refers to the result of branching: the duplication of an object under version control for further separate modification.
- byzantine agreement (byzantine-agreement)
- (non PoW) Byzantine Agreement is byzantine-fault-tolerance of distributed computing systems that enable them to come to consensus despite arbitrary behavior from a fraction of the nodes in the network. BA consensus makes no assumptions about the behavior of nodes in the system. Practical Byzantine Fault Tolerance (pBFT) is the prototypical model for Byzantine agreement, and it can reach consensus fast and efficiently while concurrently decoupling consensus from resources (i.e., financial stake in PoS or electricity in PoW).
- byzantine-fault tolerance (byzantine-fault-tolerance)
- A Byzantine fault (also interactive consistency, source congruency, error avalanche, byzantine-agreement problem, Byzantine generals problem, and Byzantine failure) is a condition of a computer system, particularly distributed computing systems, where components may fail and there is imperfect information on whether a component has failed.
- canonicalization (canonicalization)
-
In computer science, canonicalization (sometimes standardization or normalization) is a process for converting data that has more than one possible representation into a “standard,” “normal,” or canonical form.
-
This can be done to compare different representations for equivalence, to count the number of distinct data structures, to improve the efficiency of various algorithms by eliminating repeated calculations, or to make it possible to impose a meaningful sorting order.
-
More on source Wikipedia
- CBOR (CBOR)
- concise-binary-object-representation
- certificate transparency (certificate-transparency)
- Certificate Transparency (CT) is an Internet security standard and open source framework for monitoring and auditing digital certificates. The standard creates a system of public logs that seek to eventually record all certificates issued by publicly trusted certificate authorities, allowing efficient identification of mistakenly or maliciously issued certificates. As of 2021, Certificate Transparency is mandatory for all SSL/TLS certificates.
- chain of custody (chain-of-custody)
- From Wikipedia (Source):
- Chain of custody (CoC), in legal contexts, is the chronological documentation or paper trail that records the sequence of custody, control, transfer, analysis, and disposition of materials, including physical or electronic evidence. Of particular importance in criminal cases, the concept is also applied in civil litigation and more broadly in drug testing of athletes and in supply chain management, e.g. to improve the traceability of food products, or to provide assurances that wood products originate from sustainably managed forests.
- challenge-message (Challenge Message)
- A message sent and responded to during an Identity Authentication session.
- claim (claim)
- An assertion of the truth of something, typically one which is disputed or in doubt. A set of claims might convey personally identifying information: name, address, date of birth and citizenship, for example. (Source).
- clone (clone)
- A copy of a system that is - and works exactly as the original
- cloud agent (cloud-agent)
- Cloud agent is software that is installed on the cloud server instances in order to provide security, monitoring, and analysis solutions for the cloud. They actually provide information and helps to provide control over cloud entities.
- Paraphrased by @henkvancann based on source.
- Also see agent.
- code table (code-table)
- a code table is the Internet’s most comprehensive yet simple resource for browsing and searching for alt codes, ascii codes, entities in html, unicode characters, and unicode groups and categories.
- Source
- collision (collision)
-
In cryptography and identity collision generally refers to something going wrong because an identical result has been produced but it refers to - or points to - different sources or assets backing this result.
-
E.g. two hashes collide, meaning two different digital sources produce the same hash.
-
Another example is name(space) collision.
- complementary integrity verification (complementary-integrity-verification)
- A mechanism that can verify integrity independent of needing access to a previous instance or reference version of the information for comparison.
- Source: Neil Thomson
- concatenation (concatenation)
- In formal language theory and computer programming, string concatenation is the operation of joining character strings end-to-end. For example, the concatenation of “snow” and “ball” is “snowball”.
- More on source Wikipedia page
- concise-binary-object-representation
-
It is a binary data serialization format loosely based on JSON authored by C. Bormann. Like JSON it allows the transmission of data objects that contain name–value pairs, but in a more concise manner. This increases processing and transfer speeds at the cost of human readability.
-
Also knows as: CBOR
- confidentiality (confidentiality)
- All statements in a conversation are only known by the parties to that conversation.
- Source: Samuel Smith, at IIW-37, Oct 2023.
- configuration files (configuration-files)
-
In computing, configuration files (commonly known simply as config files) are files used to configure the parameters and initial settings for some computer programs. They are used for user applications, server processes and operating system settings.
-
More on source Wikipedia
- consensus mechanism (consensus-mechanism)
- How groups of entitities come to decisions. In general to learn about consensus mechanisms read any textbook on decision making, automated reasoning, multi-objective decision making, operations research etc.
- content-addressable hash (content-addressable-hash)
-
Finding content by a hash of this content, generated by a one-way hash function applied to the content.
-
Content addressing is a way to find data in a network using its content rather than its location. The way we do is by taking the content of the content and hashing it. Try uploading an image to IPFS and get the hash using the below button.
- coroutines (coroutines)
- Computer programs that can be suspended and resumed at will.
- CRUD (CRUD)
-
Is acronym for the traditional client-server database update policy is CRUD (Create, Read, Update, Delete).
-
CRUD as opposed to RUN which is the acronym for the new peer-to-peer end-verifiable monotonic update policy.
- crypto libraries (crypto-libraries)
- Cryptography libraries deal with cryptography algorithms and have API function calls to each of the supported features.
- cryptocurrency (cryptocurrency)
- A digital asset designed to work as a medium of exchange wherein individual coin ownership records are stored in a digital ledger or computerized database using strong cryptography to secure transaction record entries, to control the creation of additional digital coin records.
- See more on source Wikipedia.
- cryptographic commitment scheme (cryptographic-commitment-scheme)
-
is a cryptographic primitive that allows one to commit to a chosen value (or chosen statement) while keeping it hidden to others, with the ability to reveal the committed value later.
-
Commitment schemes are designed so that a party cannot change the value or statement after they have committed to it: that is, commitment schemes are binding.
-
More on wikipedia
- Cryptographic Primitive (cryptographic-primitive)
- the serialization of a value associated with a cryptographic operation including but not limited to a digest (hash), a salt, a seed, a private key, a public key, or a signature.
- Source: Dr. S.Smith, 2024
- cryptographic strength (cryptographic-strength)
- The term “cryptographically strong” is often used to describe an encryption algorithm, and implies, in comparison to some other algorithm (which is thus cryptographically weak), greater resistance to attack. But it can also be used to describe hashing and unique identifier and filename creation algorithms.
- More on Wikipedia
- cryptonym (cryptonym)
- a cryptographic pseudonymous identifier represented by a string of characters derived from a random or pseudo-random secret seed or salt via a one-way cryptographic function with a sufficiently high degree of cryptographic strength (e.g., 128 bits, see appendix on cryptographic-strength. A cryptonym is a type of primitive.
- CSPRNG (CSPRNG)
- means “Cryptographically Secure Pseudorandom Number Generator,” which means that a sequence of numbers (bits, bytes…) that is produced from an algorithm that is deterministic (the sequence is generated from some unknown internal state), hence pseudorandom is also cryptographically secure, or not.
- (Source: https://crypto.stackexchange.com/questions/12436/what-is-the-difference-between-csprng-and-prng)
- CT (CT)
- certificate-transparency
- DAG (DAG)
- directed-acyclic-graph
- data anchor (data-anchor)
- Data anchors are digest of digital data, that uniquely identify this data. The digest is the anchor and can be used to identify - and point to the data at the same time.
- decentralized identifier (decentralized-identifier)
-
Decentralized identifiers (DID) are a new type of identifier that enables verifiable, decentralized digital identity. A DID refers to any subject (e.g., a person, organization, thing, data model, abstract entity, etc.) as determined by the controller of the DID.
-
More technical notion: decentralized identifier
-
As known as: DID
- decentralized identity (decentralized-identity)
-
is a technology that uses cryptography to allow individuals to create and control their own unique identifiers. They can use these identifiers to obtain
Verifiable Credentialsfrom trusted organizations and, subsequently, present elements of these credentials as proof of claims about themselves. In this model, the individual takes ownership of their own identity and does not need to cede control to centralized service providers or companies. -
TrustoverIP related decentralized identity
-
KERI related decentralized identity
- decentralized key-management infrastructure (decentralized-key-management-infrastructure)
- a key management infrastructure that does not rely on a single entity for the integrity and security of the system as a whole. Trust in a DKMI is decentralized through the use of technologies that make it possible for geographically and politically disparate entities to reach an agreement on the key state of an identifier DPKI.
- Source: Dr. S.Smith, 2024
- DHT (DHT)
- distributed-hash-table
- DIDs (DID)
- decentralized-identifier
- digest (digest)
- verifiable cryptographic commitment. It’s a collision-resistant hash of content.
- digital signature (digital-signature)
- A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents. A valid digital signature, where the prerequisites are satisfied, gives a recipient very strong reason to believe that the message was created by a known sender (authentication), and that the message was not altered in transit (integrity).
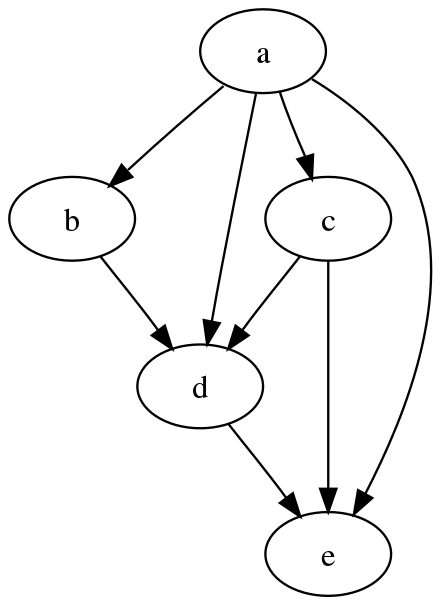
- directed acyclic graph (directed-acyclic-graph)
-
From Wikipedia (source):
-
In mathematics, particularly graph theory, and computer science, a directed acyclic graph (DAG /ˈdæɡ/ (listen)) is a directed graph with no directed cycles. That is, it consists of vertices and edges (also called arcs), with each edge directed from one vertex to another.
-
- distributed hash table (distributed-hash-table)
- It is a distributed system that provides a lookup service similar to a hash table: key-value pairs are stored in a DHT, and any participating node can efficiently retrieve the value associated with a given key. The main advantage of a DHT is that nodes can be added or removed with minimum work around re-distributing keys.
- DKPI (dkmi, dkpi, DKMI)
-
More in extended KERI glossary
- domain name (domain-name)
- A domain name is a string that identifies a realm of administrative autonomy, authority or control within the Internet. Domain names are used in various networking contexts and for application-specific naming and addressing purposes.
- More on Source Wikipedia.
- double-spend proof (double-spend-proof)
- Total global ordering of transactions so that value can’t be spent twice at the same time from the unit of value. Or in everyday language: you can’t spend your money twice.
- E2E (E2E)
- end-to-end
- eclipse attack (eclipse-attack)
-
An eclipse attack is a peer-to-peer network-based attack. Eclipse attack can only be performed on nodes that accept incoming connections from other nodes, and not all nodes accept incoming connections.
-
In a bitcoin network, by default, there are a maximum of 117 incoming TCP connections and 8 outgoing TCP connections.
- electronic signature (electronic-signature)
- An electronic signature, or e-signature, refers to data in electronic form, which is logically associated with other data in electronic form and which is used by the signatory to sign. This type of signature has the same legal standing as a handwritten signature as long as it adheres to the requirements of the specific regulation under which it was created (e.g., eIDAS in the European Union, NIST-DSS in the USA or ZertES in Switzerland).
- end to end (end-to-end)
-
Inter-host communication and data flow transformations, considered in motion and at rest.
-
- E2E Security. Inter-host communication must be end-to-end signed/encrypted and data must be stored signed/encrypted. Data is signed/encrypted in motion and at rest.
-
- E2E Provenance. Data flow transformations must be end-to-end provenanced using verifiable data items (verifiable data chains or VCs). Every change shall be provenanced.
-
Paraphrased from source Universal Identifier Theory by Samuel Smith
- entity (entity)
- entity in the #essiflab glossary.
- entropy (entropy)
- Unpredictable information. Often used as a secret or as input to a key generation algorithm.
- ephemeral (ephemeral)
- Lasting for a markedly brief time. Having a short lifespan.
- In the context of identifiers is often referred to as identifiers for one time use; or throw-away identifiers.
- escrow (escrow)
-
‘Escrow’ as a noun is a (legal) arrangement in which a third party temporarily holds money or property until a particular condition has been met.
-
‘Escrow’ as a verb: we use it in protocol design to handle out of order events. Store the event and wait for the other stuff to show up and then continue processing of the event. So escrowing is the process of storing this event. We root back to the event later.
- extensible business reporting language (extensible-business-reporting-language)
- XBRL is the open international standard for digital business reporting, managed by a global not for profit consortium, XBRL International.
- FFI (FFI)
- foreign-function-interface
- foreign function interface (foreign-function-interface)
- Is a mechanism by which a program written in one, usually an interpreted (scripted), programming language that can call routines or make use of services written or compiled in another one.
- More on Source: https://en.wikipedia.org/wiki/Foreign_function_interface
- GLEIF (GLEIF)
- Global Legal Entity Identifier Foundation
- gnu privacy guard (gnu-privacy-guard)
- also GnuPG; is a free-software replacement for Symantec’s PGP cryptographic software suite. It is compliant with RFC 4880, the IETF standards-track specification of OpenPGP. Modern versions of PGP are interoperable with GnuPG and other OpenPGP-compliant systems.
- More on wikipedia
- See more about the closely related and often-confusing term PGP.
- governance framework (governance-framework)
- Also called ‘Governance structure’. Governance frameworks are the structure of a government and reflect the interrelated relationships, factors, and other influences upon the institution. Governance frameworks structure and delineate power and the governing or management roles in an organization. They also set rules, procedures, and other informational guidelines.
- More in source Wikipedia.
- GPG (GPG)
- gnu-privacy-guard
- hardware security module (hardware-security-module)
- A HSM is a physical computing device that safeguards and manages secrets (most importantly digital keys), performs encryption and decryption functions for digital signatures, strong authenticity and other cryptographic functions.
- More in source Wikipedia
- hierarchical asynchronous coroutines and input output (hierarchical-asynchronous-coroutines-and-input-output)
-
HIO is an acronym which stands for ‘Weightless hierarchical asynchronous coroutines and I/O in Python’.
-
It’s Rich Flow Based Programming Hierarchical Structured Concurrency with Asynchronous IO. That mouthful of terms has been explained further on Github.
-
HIO builds on very early work on hierarchical structured concurrency with lifecycle contexts from ioflo, ioflo github, and ioflo manuals.
- hierchical deterministic keys (hierchical-deterministic-keys)
- An HDK type is a deterministic Bitcoin wallet derived from a known seed that allows child keys to be created from the parent key. Because the child key is generated from a known seed, a relationship between the child and parent keys is invisible to anyone without that seed.
- hio (hio)
- Weightless hierarchical asynchronous coroutines and I/O in Python.
- Rich Flow Based Programming Hierarchical Structured Concurrency with Asynchronous IO.
- HSM (HSM)
- hardware-security-module
- I O (I-O)
- input-output
- IANA (IANA)
- internet-assigned-numbers-authority
- identifier (identifier)
- Something to uniquely identify (public) identities; pointing to something or someone else.
- identifier system (identifier-system)
- a system for uniquely identifying (public) identities
- identity (identity)
- A unique entity. Typically represented by a unique identifier.
- inconsistency (inconsistency)
- If a reason, idea, opinion, etc. is inconsistent, different parts of it do not agree, or it does not agree with something else. Data inconsistency occurs when similar data is kept in different formats in more than one file. When this happens, it is important to match the data between files.
- input output (input-output)
- In computing, input/output (I/O, or informally io or IO) is the communication between an information processing system, such as a computer, and the outside world, possibly a human or another information processing system. Inputs are the signals or data received by the system and outputs are the signals or data sent from it. The term can also be used as part of an action; to “perform I/O” is to perform an input or output operation.
- integrity
- Integrity (of a message or data) means that the information is whole, sound, and unimpaired (not necessarily correct). It means nothing is missing from the information; it is complete and in intended good order.
- Source: Neil Thomson
- internal inconsistency (internal-inconsistency)
-
Internal is used to describe things that exist or happen inside an entity. In our scope of digital identifier its (in)consistency is considered within the defining data structures and related data stores.
-
In key-event-receipt-infrastructure, you are protected against internal inconsistency by the hash chain data structure of the key-event-log because the only authority that can sign the log is the controller itself.
- is the organization that oversees the allocation of IP addresses to internet service providers (ISPs).
- Source
- interoperability (interoperability)
- Interoperability is a characteristic of a product or system to work with other products or systems. While the term was initially defined for information technology or systems engineering services to allow for information exchange.
- More on source Wikipedia
- interoperable (interoperable)
- interoperability
- Interplanetary Filesystem (IPFS, interplanetary-file-system)
-
The InterPlanetary File System (IPFS) is a protocol, hypermedia and file sharing peer-to-peer network for sharing data using a distributed hash table to store provider information.
-
Source wikipedia
- ip address (ip-address)
-
An Internet Protocol address (IP address) is a numerical label such as ‘192.0.2.1’ that is connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: network interface identification and location addressing.
-
Much more on source Wikipedia
- javascript object notation (javascript-object-notation)
- JSON (JavaScript Object Notation, pronounced /ˈdʒeɪsən/; also /ˈdʒeɪˌsɒn/) is an open standard file format and data interchange format that uses human-readable text to store and transmit data objects consisting of attribute–value pairs and arrays (or other serializable values). It is a common data format with diverse uses in electronic data interchange, including that of web applications with servers.
- javascript object signing and encryption (javascript-object-signing-and-encryption)
- is a framework intended to provide a method to securely transfer claims (such as authorization information) between parties. The JOSE framework provides a collection of specifications to serve this purpose.
- JOSE (JOSE)
- javascript-object-signing-and-encryption
- JSON (JSON)
- javascript-object-notation
- JSONPath
-
In computer software, JSONPath is a query language for querying values in JSON.
-
See more: Wikipedia JSONPath
- key (key)
- In our digital scope it’s a mechanism for granting or restricting access to something. MAY be used to issue and prove, MAY be used to transfer and control over identity and cryptocurrency. More
- key compromise (key-compromise)
- Basically there are three infrastructures that are included in “key management” systems that must be protected:
-
- Key pair creation and storage
-
- Event signing
-
- Event signature verification
- So when we say “key compromise” we really mean compromise of one of those three things.
- key management (key-management)
- management of cryptographic keys in a crypto-system. This includes dealing with the generation, exchange, storage, use, crypto-shredding (destruction) and replacement of keys (also #key-rotation). It includes cryptographic protocol design, key servers, user procedures, and other relevant protocols.
- key pair (keypair, key-pair)
-
is an ordered pair consisting of a public key and its corresponding private key.
-
More: is a private key and its corresponding public key resulting from a one-way crypto-graphical function; a key pair is used with an asymmetric-key (public-key) algorithm in a so called public-key-infrastructure (PKI).
- key state (key-state)
- a set of currently authoritative keypairs for an AID and any other information necessary to secure or establish control authority over an AID. This includes current keys, prior next key digests, current thresholds, prior next thresholds, witnesses, witness thresholds, and configurations.
- key stretching (key-stretching)
- In cryptography, key stretching techniques are used to make a possibly weak key, typically a password or passphrase, more secure against a brute-force attack by increasing the resources (time and possibly space) it takes to test each possible key.
- key transparency (key-transparency)
- provides a lookup service for generic records and a public, tamper-proof audit log of all record changes. While being publicly auditable, individual records are only revealed in response to queries for specific IDs.
- keypair
- key-pair
- keystore (keystore)
- A keystore in KERI is the encrypted data store that hold the private keys for a collection of AIDs.
- Source: Philip Feairheller.
- large language model (large-language-model)
- A large language model (LLM) is a language model consisting of a neural network with many parameters (typically billions of weights or more), trained on large quantities of unlabeled text using self-supervised learning or semi-supervised learning.
- More on Source Wikipedia
- lead bytes (lead-bytes)
- In order to avoid confusion with the use of the term pad character, when pre-padding with bytes that are not replaced later, we use the term lead bytes. So lead-bytes are added “pre-conversion”.
- legal entity (legal-entity)
- Unique parties that are legally or financially responsible for the performance of financial transactions or have the legal right in their jurisdiction to enter independently into legal contracts.
- LEI (LEI)
- Legal Entity Identifier
- levels of assurance (levels-of-assurance)
- Identity and other trust decisions are often not binary. They are judgement calls. Any time that judgement is not a simple “Yes/No” answer, you have the option for levels of assurance. Also ‘LoA’.
- liveness (liveness)
- Liveness refers to a set of properties of concurrent systems, that require a system to make progress despite the fact that its concurrently executing components (“processes”) may have to “take turns” in critical sections, parts of the program that cannot be simultaneously run by multiple processes.
- LLM (LLM)
- large-language-model
- LoA (LoA)
- levels-of-assurance
- LoC (LoC)
- loci-of-control
- loci of control (loci-of-control)
- Locus of control is the degree to which people believe that they, as opposed to external forces (beyond their influence), have control over the outcome of events in their lives. Also ‘LoC’.
- More on wikipedia
- media type (media-type)
-
A Media type (formerly known as MIME type) is a standard way to indicate the nature and format of a file, in the same way as ‘image/jpeg’ for JPEG images, used on the internet.
-
It is a two-part identifier for file formats and format contents transmitted on the internet. Their purpose is somewhat similar to file extensions in that they identify the intended data format.
- message (message)
- a serialized data structure that comprises its body and a set of serialized data structures that are its attachments. Attachments may include but are not limited to signatures on the body.
- Source: Dr. S.Smith
- messagepack (messagepack)
- MessagePack is a computer data interchange format. It is a binary form for representing simple data structures like arrays and associative arrays. MessagePack aims to be as compact and simple as possible. The official implementation is available in a variety of languages
- MFA (MFA)
- multi-factor-authentication
- MIME type (MIME-type)
- media-type
- multi-factor authentication (multi-factor-authentication)
- Authentication by combining multiple security factors. Well-known factors are what you know, what you have and what you are.
- multicodec (multicodec)
-
Is a self-describing multi-format, it wraps other formats with a tiny bit of self-description. A multi-codec identifier is both a variant (variable length integer) and the code identifying data.
-
See more at GitHub Multi-codec
- multiplexing (multiplexing)
- In telecommunications and computer networking, multiplexing (sometimes contracted to muxing) is a method by which multiple analog or digital signals are combined into one signal over a shared medium. The aim is to share a scarce resource - a physical transmission medium.
- More on source Wikipedia-page
- multisig (multisig)
- also multi-signature or multisignature; is a digital signature scheme which allows a group of users to sign a single piece of digital data.
- Paraphrased by @henkvancann from Wikipedia source
- namespace (namespace)
- In an identity system, an identifier can be generalized to a namespace to provide a systematic way of organizing identifiers for related resources and their attributes. A namespace is a grouping of symbols or identifiers for a set of related objects.
- NFT (NFT)
- non-fungible-token
- non normative (non-normative)
- A theory is called non-normative if it does not do what has described under ‘normative’. In general, the purpose of non-normative theories is not to give answers, but rather to describe possibilities or predict what might happen as a result of certain actions.
- Source.
- non-disclosure-agreement (NDA, Non-Disclosure Agreement)
- An agreement that outlines requirements for handling confidential information
- non-fungible token (non-fungible-token)
- A non-fungible token (NFT) is a financial security consisting of digital data stored in a blockchain, a form of distributed ledger.
- normative (normative)
- a theory is “normative” if it, in some sense, tells you what you should do - what action you should take. If it includes a usable procedure for determining the optimal action in a given scenario.
- Source.
- one-way function (one-way-function)
- In computer science, a one-way function is a function that is easy to compute on every input, but hard to invert given the image of a random input. Here, “easy” and “hard” are to be understood in the sense of computational complexity theory, specifically the theory of polynomial time problems.
- More on Wikipedia
- owner (owner)
- Owner in ToIP glossary
- ownership (ownership)
- Ownership in ToIP glossary
- P2P (P2P)
- peer-to-peer
- pad (pad)
- is a character used to fill empty space, because many applications have fields that must be a particular length.
- Source
- passcode (passcode)
- A password, sometimes called a passcode (for example in Apple devices), is secret data, typically a string of characters, usually used to confirm a user’s identity.
- More on source Wikipedia
- payload (payload)
- The term ‘payload’ is used to distinguish between the ‘interesting’ information in a chunk of data or similar and the overhead to support it. The payload refers to the interesting part.
- pdf-document (pdf)
- A document in the standard portable document format “pdf”-format
- peer to peer (peer-to-peer)
-
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network. They are said to form a peer-to-peer network of nodes
-
More on source Wikipedia
- perfect security (perfect-security)
- a special case of Information theoretic security itps.
- Source: Dr. S. Smith
- persistent data structure (persistent-data-structure)
- An append only verifiable data structure. What we sign may not change.
- PGP (PGP)
- pretty-good-privacy
- pipelining (pipelining)
- In computing, a pipeline, also known as a data pipeline, is a set of data processing elements connected in series, where the output of one element is the input of the next one. The elements of a pipeline are often executed in parallel or in time-sliced fashion. Some amount of buffer storage is often inserted between elements.
- More on source Wikipedia-page
- PKI (PKI)
- public-key-infrastructure
- post pad (post-pad)
- the action and / or result of extending a string with trailing pad characters to align to a certain length in bits or bytes.
- post quantum (post-quantum)
- In cryptography, post-quantum cryptography (PQC) (sometimes referred to as quantum-proof, quantum-safe or quantum-resistant) refers to cryptographic algorithms (usually public-key algorithms) that are thought to be secure against a cryptanalytic attack by a quantum computer.
- More on source Wikipedia
- pre pad (pre-pad)
- the action and / or result of prepending a string with leading pad characters to align to a certain length in bits or bytes.
- pretty good privacy (pretty-good-privacy)
- Is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. Phil Zimmermann developed PGP in 1991.
- More on wikipedia
- So also the often confusing GPG term.
- primitive (primitive)
- a serialization of a unitary value. All Primitives in KERI must be expressed in composable-event-streaming-representation.
- Source: Dr. S.Smith
- privacy (privacy)
-
Privacy is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively.
-
The domain of privacy partially overlaps with security, which can include the concepts of appropriate use and protection of information. Privacy may also take the form of bodily integrity.
-
More on source Wikipedia
- PRNG (PRNG)
-
means “Pseudorandom Number Generator” which means that a sequence of numbers (bits, bytes…) is produced from an algorithm which looks random, but is in fact deterministic (the sequence is generated from some unknown internal state), hence pseudorandom.
-
Such pseudorandomness can be cryptographically secure, or not. It is cryptographically secure if nobody can reliably distinguish the output from true randomness, even if the PRNG algorithm is perfectly known (but not its internal state). A non-cryptographically secure PRNG would fool basic statistical tests but can be distinguished from true randomness by an intelligent attacker.
-
(Source: https://crypto.stackexchange.com/questions/12436/what-is-the-difference-between-csprng-and-prng)
- Proof that somebody or something has certain rights or permissions. It’s about data. Whereas proof-of-authorship is about data and its original creator.
- A proof-of-authority provides verifiable authorizations or permissions or rights or credentials.
- protocol (protocol)
- Generic term to describe a code of correct conduct. Also called “etiquette”: a code of personal behavior.
- provenance (provenance)
-
From Wikipedia (Source):
-
Provenance (from the French provenir, ‘to come from/forth’) is the chronology of the ownership, custody or location of a historical object. The term was originally mostly used in relation to works of art but is now used in similar senses in a wide range of fields, including archaeology, paleontology, archives, manuscripts, printed books, the circular economy, and science and computing.
- pseudo-random number (pseudo-random-number)
- A (set of) value(s) or element(s) that is statistically random, but it is derived from a known starting point and is typically repeated over and over.
- public key infrastructure (public-key-infrastructure)
-
Is a set of roles, policies, hardware, software and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption.
-
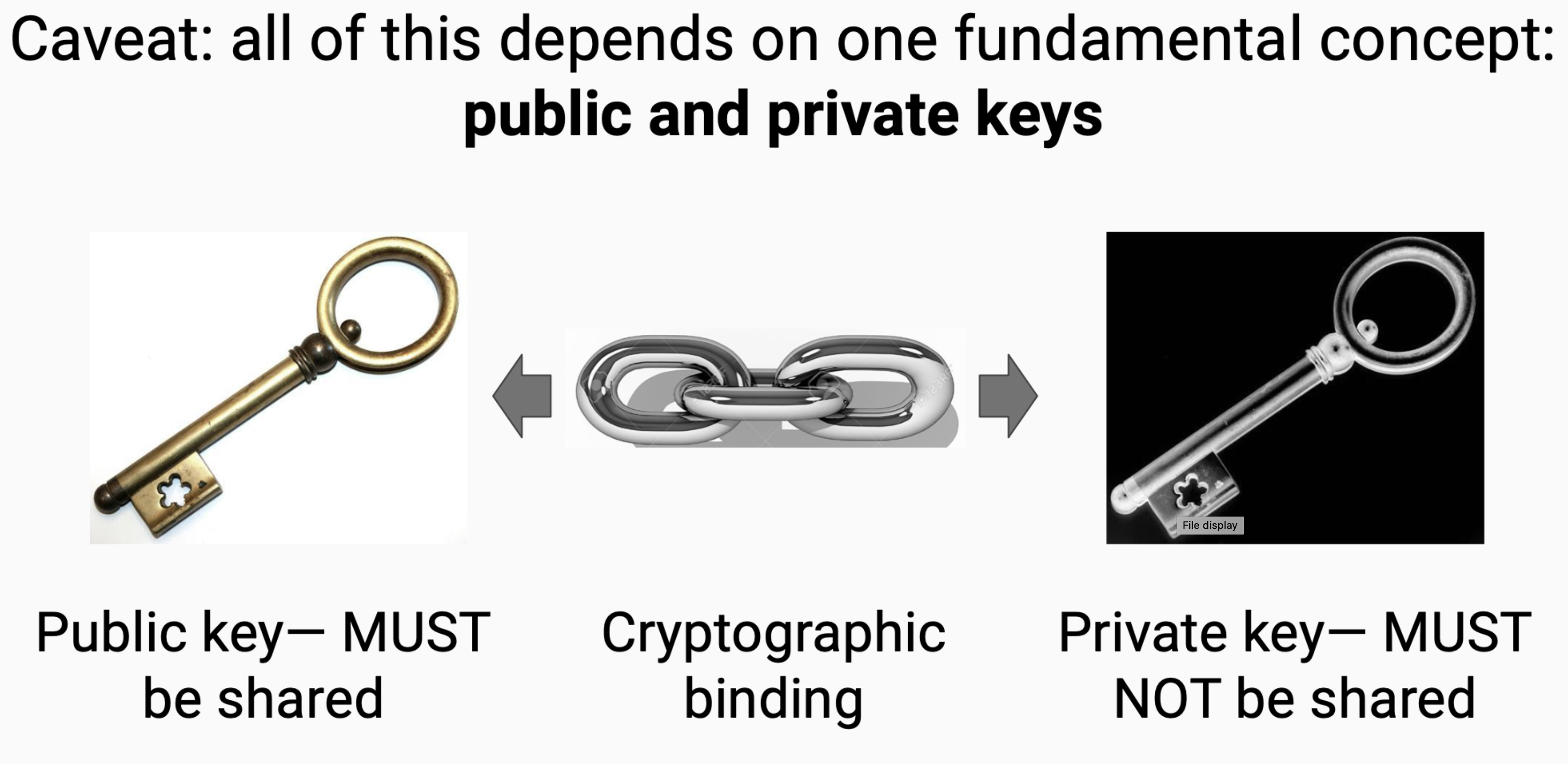
-
More on Wikipedia
- race condition (race-condition)
- A race condition or race hazard is the condition of an electronics, software, or other system where the system’s substantive behavior is dependent on the sequence or timing of other uncontrollable events. It becomes a bug when one or more of the possible behaviors is undesirable.
- Source.
- rainbow table attack (rainbow-table-attack)
- A rainbow table attack is a password-cracking method that uses a special table (a “rainbow table”) to crack the password hashes in a database.
- registry (registry)
- In our digital mental model it’s an official digital record book. When people refer to a registry, they usually mean a specific instance, within a multi-tenant registry. E.g. Docker Hub is a multi-tenant registry, where there’s a set of official / public images.
- replay attack (replay-attack)
- A replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants.
- repo (repo)
- Software is our line of work. In this, ‘repo’ is the short hand for ‘Repository’, mostly referring to a software repo(sitory) on Github.com, Gitlab (https://gitlab.com) or other software repository hosting services.
- revocation (revocation)
- Revocation is the act of recall or annulment. It is the cancelling of an act, the recalling of a grant or privilege, or the making void of some deed previously existing.
- More on source Wikipedia
- ricardian contract (ricardian-contract)
- The Ricardian contract, as invented by Ian Grigg in 1996, is a method of recording a document as a contract at law, and linking it securely to other systems, such as accounting, for the contract as an issuance of value.
- root of trust (root-of-trust)
- A root-of-trust is some component of a system that is security by design and its security characteristics may be inherently trusted or relied upon by other components of the system.
- salt (salt)
- random data fed as an additional input to a one-way function that hashes data.
- Source: Dr. S. Smith
- schema namespace registry (schema-namespace-registry)
- a centrally managed schema-registry where corporations or individuals reserve schemas within a specific namespace in order to have an interoperable schema that is labeled with a corporation-specific or individual-specific namespace.
- schema registry (schema-registry)
- Central registry for credential schemas based on namespaces.
- seal (seal)
- a seal is a cryptographic commitment in the form of a cryptographic digest or hash tree root (Merkle root) that anchors arbitrary data or a tree of hashes of arbitrary data to a particular event in the key event sequence.
- Source: Dr. S. Smith
- security overlay properties trillema (security-overlay-properties-trillema)
- An identifier system has some degree of any combination of the three properties authenticity, privacy and confidentiality, but not all three completely.
- seed (seed)
- In cryptography a ‘seed’ is a pseudorandomly generated number, often expressed in representation of a series of words.
- Paraphrased from wikipedia
- self sovereignty (self-sovereignty)
- Self sovereignty in Trust over IP wiki.
- semver (semver)
- Semantic Versioning Specification 2.0. See also (https://semver.org/)[https://semver.org/].
- Source: Dr. S.Smith
- service endpoint (service-endpoint)
- In our context we consider a web service endpoint which is a uniform-resource-locator at which clients of specific service can get access to the service.
- Service Level Agreement (SLA, service-level-agreement)
-
A document that contains detailed descriptions of the services to be provided by service parties and the service level requirements expected for these services.
-
Source verifiable LEI (vLEI) Ecosystem Governance Framework Glossary
- side-channel attack (side-channel-attack)
-
any attack that extracts secrets by observing indirect information leaked by a system — things like how long it takes to do an operation, how much power it uses, emitted radio/EM noise, cache behavior, or even tiny sounds — rather than breaking the cryptography or protocol directly.
-
More: Wikipedia
- signed digest (signed-digest)
- commitment to content, by digitally signing a digest of this content.
- signing threshold (signing-threshold)
- Is the minimum number of valid signatures to satisfy the requirement for successful verification in a threshold-signature-scheme.
- source of truth (source-of-truth)
- The source of truth is a trusted data source that gives a complete picture of the data object as a whole.
- Source: LinkedIN.
- spanning layer (spanning-layer)
-
An all encompassing layer horizontal layer in a software architecture. Each trust layer only spans platform specific applications. It bifurcates the internet trust map into domain silos (e.g. twitter.com), because there is no spanning trust layer.
-

- SSL
- See: Secure Sockets Layer.
- SSL (Secure Sockets Layer)
-
The original transport layer security protocol developed by Netscape and partners. Now deprecated in favor of Transport Layer Security (TLS).
-
Also known as: SSL.
- sub shell (sub-shell)
- A subshell is basically a new shell just to run a desired program. A subshell can access the global variables set by the ‘parent shell’ but not the local variables. Any changes made by a subshell to a global variable is not passed to the parent shell.
- Source
- supermajority (supermajority)
- Sufficient majority that is labeled immune from certain kinds of attacks or faults.
- TCP
- transmission-control-protocol
- TCP (Transmission Control Protocol)
-
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliable, ordered, and error-checked delivery of a stream of octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP, which is part of the Transport Layer of the TCP/IP suite. SSL/TLS often runs on top of TCP.
-
Source: Wikipedia.
-
Also known as: TCP.
-
See also: User Datagram Protocol.
- tcp endpoint (tcp-endpoint)
- This is a service-endpoint of the web transmission-control-protocol
- TEE (TEE)
- trusted-execution-environment
- threshold structure security (threshold-structure-security)
- A threshold structure for security allows for weaker key management or execution environment infrastructure individually, but achieve greater overall security by multiplying the number of attack surfaces that an attacker must overcome to compromise a system.
- TPM (TPM)
- trusted-platform-module
- trans-contextual value (trans-contextual-value)
- Value that is transferrable between contexts. How do we recapture the value in our data? 1- Leverage cooperative network effects 2- Retake control of our data.
- Source Samuel Smith
- Tritet (tritet)
- 3 bits. See Performant resynchronization with unique start bits.
- Source: Dr. S. Smith
- trusted execution environment (trusted-execution-environment)
- Protected hardware/software/firmware security system. The controller may protect its key generation, key storage, and event signing infrastructure by running it inside a trusted execution environment (TEE).
- trusted platform module (trusted-platform-module)
-
A device that enhances the security and privacy (of identity systems) by providing hardware-based cryptographic functions.
-
§ Functions
-
A TPM can generate, store, and protect encryption keys and authentication credentials that are used to verify the identity of a user or a device.
-
A TPM can also measure and attest the integrity of the software and firmware that are running on a system, to ensure that they have not been tampered with or compromised.
-
§ Form
-
A TPM can be implemented as a physical chip, a firmware module, or a virtual device.
-
Source: Bing chat sept 2023
- ts node (ts-node)
- npm package that lets you run typescript from a shell
- UI (UI)
- user-interface
- uniform resource locator (uniform-resource-locator)
- A Uniform Resource Locator (URL), colloquially termed a web address, is a reference to a web resource that specifies its location on a computer network and a mechanism for retrieving it.
- URL (URL)
- uniform-resource-locator
- user interface (user-interface)
- A user interface (UI or U/I) is the space where interactions between humans and machines occur.
- validate (validate)
- ESSIF-lab definition of validate. Although this definition is very general, in the KERI/ACDC vocabulary, ‘validate’ currently has extra diverse meanings extending the one of eSSIF-lab, such as
-
- evaluate
- validators (validator)
- any entity or agent that evaluates whether or not a given signed statement as attributed to an identifier is valid at the time of its issuance.
- Source: Dr. S. Smith
- variable length (variable-length)
- a type of count code allowing for vaiable size signatures or attachments which can be parsed to get the full size.
- Source: Dr. S. Smith
- VC (VC)
- verifiable-credential
- VDS (VDS)
- verifiable-data-structure
- veracity (veracity)
- The quality of being true; contrast authenticity. When a newspaper publishes a story about an event, every faithful reproduction of that story may be authentic — but that does not mean the story was true (has veracity).
- verifiable data registry (verifiable-data-registry)
- A role a system might perform by mediating issuance and verification of ACDCs. See verifiable data registry.
- Source: Dr. S. Smith
- verifiable data structure (verifiable-data-structure)
- A verifiable data structure is a data structure that incorporates cryptographic techniques to ensure the integrity and authenticity of its contents. It allows users to verify the correctness of the data stored within the structure without relying on a trusted third party.
- #Sources-Definition-ChatGPT
- verified integrity (verified-integrity)
- A mechanism that can unambiguously assess whether the information is/continues to be whole, sound and unimpaired
- verifier (verifier)
- any entity or agent that cryptographically verifies the signature(s) and digests on an event Message.
- Source Dr. S. Smith
- verify signature (verify-signature)
- Applying an algorithm that, given the message, public key and signature, either accepts or rejects the message’s claim to authenticity.
- wallet (wallet)
- A crypto wallet is a device, physical medium, program or a service which stores the public and/or private keys for cryptocurrency transactions and digital identifiers.
- Paraphrased by @henkvancann from source Wikipedia
- web of trust (web-of-trust)
- In cryptography, a web of trust is a concept used in PGP, gnu-privacy-guard, and other
OpenPGP-compatible systems to establish the authenticity of the binding between a public key and its owner. - XBRL (XBRL)
- extensible-business-reporting-language
- zero trust (zero-trust)
- a Zero Trust approach trusts no one.
- zero-trust computing (zero-trust-computing)
- A security model centered on the principle of “never trust, always verify.” It assumes that threats can exist inside and outside the network, and thus, no entity — a device, user, or system — is inherently trusted. This approach requires continuous verification of all users and devices attempting to access network resources.